*FUD also stands for “Fully UnDetectable”, which describes malware that evades the bulk of commercially used antivirus products.
PEN-300 naturally continues where PEN-200 leaves off, for more advanced techniques. After all, OSCP skills alone will not beat modern mitigations; we must try harder.
What Do I Really Need Before PEN-300?
There has been a trend in Offensive Security courses where students take other courses to prepare them for what Offensive Security has to offer. For me, I came in with some existing background having attained the CRTP from Pentester Academy to bridge the gap between the old OSCP certification and the new OSCP certification. Others may have taken the CRTO from ZeroPoint Security. The prevailing view is that these courses help one be comfortable, but are not strictly required.
Broadly, there are two main parts to PEN-300:
– Evasion of defences like Windows Defender, Fileless Malware Implementation (e.g. reflection)
– Additional exploitation techniques such as domain misconfigurations, DevOps implementations
There are other supplementary chapters (e.g. kiosk breakouts, domain-fronting attacks), but these are icing on the cake. The bread and butter will be a repertoire of tricks to get initial access, bypassing Windows (mostly) defences and lateral movement. A Cyber Kill Chain helps understand these in perspective.
The course expects little familiarity with C# or Powershell. Thankfully, picking up C# is easy because of how easy it is to read, and how powerful it is.
Expect to do plenty of reading throughout the course as the course encourages you to develop your own techniques through the extra miles. Some handy reading material can be found here (nullg0re also has a course review here, which is an encouraging read) and there. Reading is best done alongside doing the lab exercises.
Is This *NOT* A Red Team Course?
Some people describe a “pentesting” role the same as a “red teaming” one. Others take “red team” to mean Active Directory. Here is a collection of screenshots that sums up the confusion on “red teaming”. Given the diversity in thoughts about “red team”, it is clear that there is confusion.

From Morten’s reply, red teams take into account an active team monitoring mitigations and controls, as opposed to a penetration test, which is a technical assessment. Unfortunately, the terms “red team” and “penetration test” have suffered a similar fate as the terms “vulnerability assessment” and “penetration test” in the working world, especially among people unfamiliar with the subject.
In other words, the PEN-300 is a penetration testing course and Offensive Security teaches this with a penetration testing objective in mind. I mentioned briefly in my CRTP review what I felt was a misnomer in the phrase “red team” used too liberally in the industry.
Office Macros?
The first part of the course revolves around improving tradecraft to (i) write payloads in different formats and (ii) developing them to bypass a variety of defences.
MSDN and P/Invoke dominated the initial stages of the course. Basically, whenever we want to invoke a Win32 API in the .NET framework, we need to declare it, together with the data types of the arguments it accepts. P/Invoke tells us how to invoke these API calls whereas MSDN provides us information about the APIs themselves. A simple example is shown below, in Visual Basic.

The example above leverages the .NET framework in VB script. C# shellcode and POwershell shellcode also often leverages the .NET framework. As of writing this review, C# and Powershell will continue to remain hot favourites for writing Windows-based malware, but Windows’s recent posture on old Win32 APIs might encourage developers to port their FUD shellcode to other languages.
First Step of FUD: Reflection (on our abilities)
We go into many different angles of defence evasion in PEN-300. I will not describe them in detail, but I will just show one example of what you will be made to go through.

Often we enjoy using the words “fileless malware”. The technique behind “fileless malware” is reflection, where we avoid dropping malware to disk, defeating AV that does not scan in memory.
Sometimes, We Still Need Files After All
Sometimes we cannot avoid dropping files to disk. While resources on this are extremely extensive, plenty of time was spent fighting with antiscan.me while checking how “FUD” our payloads are. While antiscan.me was a good resource, it sometimes fails.
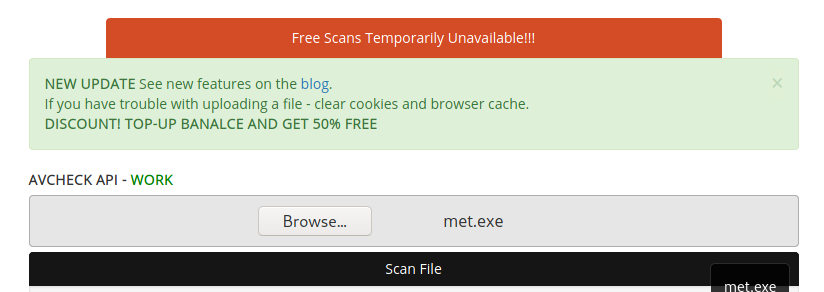
While much of the tradecraft in PEN-300 is foundational, they set the stage for further research. However, never underestimate foundational tradecraft, as can be seen in the example below:

I spent a few weeks building up my tradecraft, starting with little C# knowledge. Eventually, I grew to like C# personally. I still find VB script syntax… annoying but we cannot choose our poisons at times.
Kerberos on… Linux?
“Ah, we have Port 88 open… Kerberos… ok, this is a Windows environment,” says the naive penetration tester. Except… you can also integrate Linux machines with Kerberos log-ins.
Nowadays, Kerberos logins are ubiquitous with Windows active directory environments, but the Kerberos standard was first developed by MIT. Windows adopted it as the default log-in standard starting from Windows 2k, and while implementation on Linux is possible, it was an eye-opener how Kerberos implementation on Linux can be exploited in an almost comical way, given the correct misconfigurations. Go beyond Kekeo and Rubeus in printing tickets!
A Brief Moment of Active Directory Fun
Because of my prior background through CRTP, the next main section was easier for me, since I was already familiar with the typical TTPs in an Active Directory enumeration and compromise. This section, as opposed to the holy grail of being “FUD”, is more mechanical. Just as I described in the CRTP review, the cycle of enumeration and exploitation repeats for each account compromise.
However, the PEN-300 takes the active directory section a little differently from the CRTP. Instead of running everything off Powershell, PEN-300 uses a more foundational approach of slowly building up various tools, such as the the implementation of the PrintSpoofer privilege escalation from scratch, and a set of C# code snippets for SQL server interaction. Adding such a portion, beyond the usual Bloodhound-ing, Powerview-ing and Mimikatz-ing, provides the section with a refreshing approach at a deeper level.
Challenges: The Real Fun Begins!
The real fun begins after picking up the necessary tradecraft. Being a black box penetration testing course, enumeration and defence evasion is part and parcel of the engagement, repeatedly.

I spent about one and a half months on the challenges (out of my 90-day subscription). Leave generous amount of time for challenges; much of the learning and exam success depends on how much work you put into the challenges. The challenges are extremely effective at bridging the student from the course material chapters to a real-world penetration test, and will in turn be extremely effective at bridging the student to the examination (this is the most helpful tip I can give!)
Sometimes, the challenges prove to be a far greater stumbling block than expected; do cater time to go through them at your own pace. Long uninterrupted blocks preferred, or else you’ve to keep setting up your pivots repeatedly.
Keep notes, especially the methodology, the code snippets used and steps taken in enumeration and exploitation. That way, you will have your material to fall back on on the examination. It is normal to experience much sufferance during the challenges, but much of the learning revolves around failure and troubleshooting failure. Take notes of that as well, so you can recognise rabbit holes before falling too deep into them.
If you are time-limited, I personally recommend at least doing Challenges 5 and 6 as their sizes are more representative of a realistic domain environment. However, each challenge has its own merit and aims to combine several skills from different chapters.
Exam-Time: The OSEP
No spoilers, but some general tips.
- It’s a marathon, not a sprint. One could get by OSCP without sleep, but don’t try this on the OSEP exam. The advice is exactly the same as on my AWAE review.
- Master all your challenges (basically collect all flags). Ideally, record down, step by step, what you did in the challenges. You will find your note-taking essential.
- A network penetration test is not a CTF.
- Have fun!
There are plenty of useful code snippets that can be put together prior to the examination; some useful resources I used include https://github.com/chvancooten/OSEP-Code-Snippets. You may find other code snippets attempting to be FUD, but do not be overly obsessed with finding the best C2; I used Meterpreter for the examination and it worked (this is not a course to teach you how to use a specific C2 framework, but trying them out to find out what works and what requires tuning is helpful).
I Tried Harder, Now What?
In the AWAE review, I mentioned I would do an active directory course. Finally I have ticked that off the checklist just before my fifth work anniversary. However, much has changed since then. With the release of OSCE3, the target has probably changed and become more definitive. One more Level 300 Offensive Security course to go for!
Should I Take This Course?
If you experience this during penetration tests:

Take it. Penetration testing changes with improved defences. The OSCP establishes a foothold, but the OSEP will help expand it.