I have decided to share a post written by Naomi, a CISO, on her views on whether a cybersecurity career requires IT fundamentals. She summarises her position as follows:
You don’t NEED to know networking, computer hardware, operating systems, databases, or anything deeply technical to start in cybersecurity. All you need is a high level of comfort around technology. And you get this through constant exposure to IT.
Extracted directly from Linkedin post: https://www.linkedin.com/posts/naomi-buckwalter_cybersecurity-activity-6788161943971667968-1XuQ
I shall use her post to explain my take of the cybersecurity industry. Unfortunately, this will be a lengthy read, since there is much ground to cover.
A number of people have asked how it is possible to make a mid-career switch into cybersecurity. To answer this question properly, we need to define what a cybersecurity job is. Let us approach this from the perspective of breadth.
How Broad is the Cybersecurity Industry?
Disclaimer: I cannot possibly cover everything. I shall only write on a variety of areas, some of which I have experience in.
The Technical End
To begin, let us appreciate the breadth of the cybersecurity industry. On the technical end, there are people who perform tasks such as reverse engineering for roles such as malware analysis, source code review, vulnerability research and more. Even senior-level penetration testers need to understand some reverse engineering. There is an acute shortage of talent in this area. For instance, reverse engineering of a simple Windows executable written in C# likely requires understanding C#, the .NET framework, familiarity with a debugger/disassembler and other basics that are already assumed. Some technical roles are simply not entry level. How hard is it? Here is a summary, based of a security expert’s review of a pinnacle course in Windows exploitation:
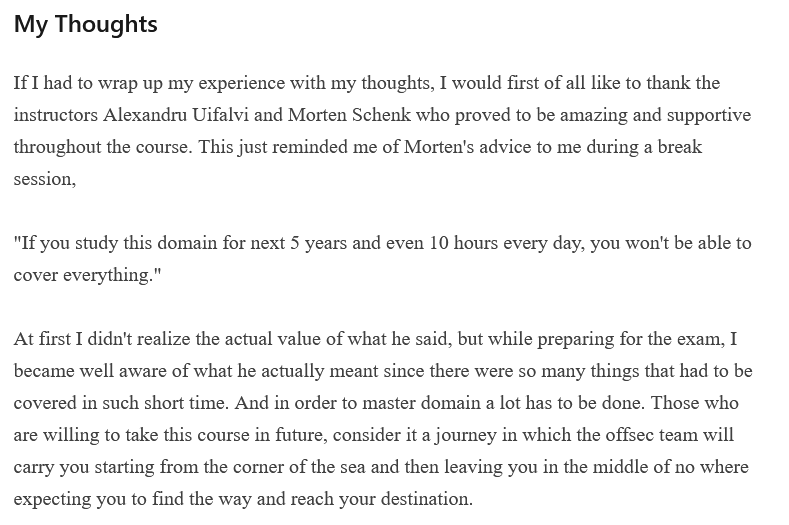
For me, I do web application and infrastructure penetration testing and vulnerability assessment. To be successful as a penetration tester, I need to understand applications of varying languages fast before being able to ask how a web application or infrastructure can be abused. There are entry-level penetration testing roles in many firms, but all of these require a curious mind, lateral thinking, and the ability to write quick and dirty code in a scripting language of choice (e.g. Python, Perl).
While the “offensive security” angle is indeed attractive, defenders are our true unsung heroes. Just as we can approach security architecture from a “defence-in-depth” perspective, we can also attempt to view the job roles of a complex cyber defence eco-system in a similar way. I shall take some time to write about the defence, since this is normally not an area that is appreciated very much.
At the perimeter (logical edge of an organisation’s IT infrastructure), there exists services that the public can access. A security architect’s role is often to design the network topology, segregate trust boundaries, and implement security devices in an economical and effective way. A working understanding of defensive capabilities and network architecture are some requirements of a typical security architect. Clearly, as IT infrastructure increasingly moves towards software-defined networks (be it cloud, DevOps orchestration), the security architect’s role is not static either. And a security architect needs to be fluent technically too.
It’s Not Just a Technical World
If security architects had their way, the organisation will most likely purchase too many firewalls, intrusion prevention systems, and hardware encryptors, which is likely to be overkill for many industries. Additionally, technically component people are highly paid, which results in additional cost to the business. Hence, businesses need to weigh security against many other factors. This offers another dimension of the cybersecurity profession.
One broad cluster in this area is the governance, risk and compliance (GRC) cluster.
Most businesses have a primary objective to be profitable. Security is often not a foremost consideration. This is why governments have had to introduce standards for firms to obey, especially if they deal with sectors deemed critical to the country’s operation of prosperity. To do so, regulations are imposed on firms to comply to security standards published by reputable firms by the Center for Internet Security (CIS). However, is compliance security? The answer is “not really”, since the business has no idea about whether its security posture is an acceptable level of risk.
To deal with risk, an understanding of the threat landscape is in order, which is typically done through a threat risk assessment (TRA). SANS has a useful read on this, and in the country I come from (Singapore), our cybersecurity agency has also prepared such a guide. A threat risk assessment can be summarised as an overview of an organisation’s attack surface, enumerating the possible ways attackers could compromise the organisation, and assessing whether the organisation’s security measures prove sufficient in defending against said threats, or mitigating the risk of an assumed breach to an acceptable enough level. A TRA is important for an organisation to understand the kind of security-related liability or trouble it could be subjected to. But how can one do a TRA without deep understanding of technology?
But cybersecurity is not just about technology. People and processes matter too, and with that, the governance of an organisation’s ability to maintain its cybersecurity posture is important. Do its people know the dangers behind charging their smartphone using the corporate laptop? Will project managers ensure their project engineers review the security posture of their systems at an acceptable rate? Daily habits contribute to the cybersecurity defence of an organisation too.
Ok, It’s Broad. Is All I Need to Do to “Try Harder”?
The “brute force” method towards trying to learn or master something is often preached in many industries, and for good reason. If the industry requires a well-defined manner of working, it could work. For instance, accounting standards do not change year-on-year (if it did, it would be a book-keeping nightmare). However, cybersecurity, no matter which area, is not simply about “brute force”. If you “try harder”, you will succeed. But what does it mean to “try harder”?
To answer this question, I shall use my own journey to answer this.
I graduated with a Physics degree, and only with the good grace of my first employer, I had an opportunity to transition to cybersecurity. In a large firm, I started understanding the cybersecurity operations and tasks of a well-established entity, realised its breadth, and spent at least the first six months catching up with my peers who were otherwise better endowed with “IT fundamentals” such as a computer engineering, computer science or electrical engineering degree. At the least, they knew what a “pointer” was because they had to deal with it in their course; a physicist uses code only to solve problems, and unless a physicist needed the quickest computation possible, there was little need to dabble in low-level languages (C/C++), resulting in the need to know what a pointer was.
Besides catching up with my peers, I took a course by Offensive Security to catch up on what the basics of penetration testing were, and have documented my journey in a three-part review (1, 2, 3). In that one year, I was nearly burnt, took a two-week vacation just to clear my mind and not touch penetration testing, and reflected on the sufferance required to catch up. However, the world of penetration testing opened my mind because I learnt what I did not know. I enjoyed it, and went on to take more Offensive Security certifications, built some deliberately vulnerable machines for public consumption and gave a few talks along the way.
In my view, “trying harder” is not about studying. It is about being able to go the extra mile to seek learning. And this is where I disagree with the original poster on her overly optimistic view on cybersecurity, where she opines the following:

Some commentators on Linkedin have pointed out the flaws on the car analogy.
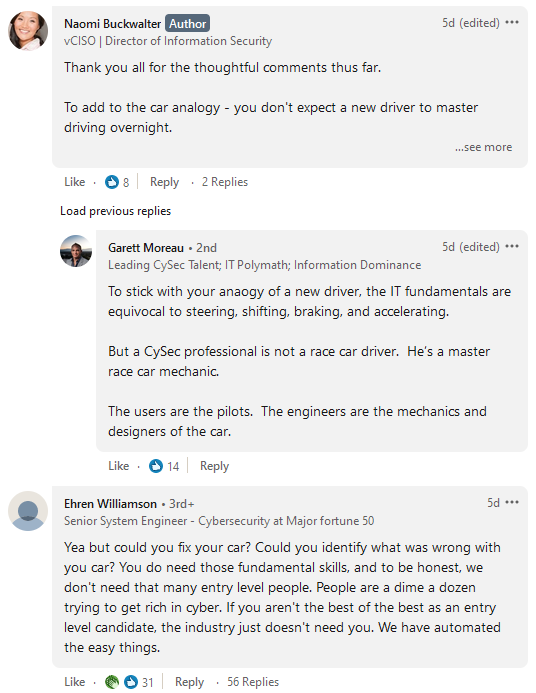
My take on this is most closely aligned to Garett Moreau, but I shall attempt to address what I think is required to survive in the cybersecurity industry.
- Curiosity, Especially With the Basics
Perhaps one area where my Physics degree helped me is in my thinking. Increasingly, the technically more challenging subject material often requires me to do my own research, read up documentation (sometimes in bits and pieces because most programmers simply do not work at such low level), and attempt to make sense of new ideas. Garett Moreau is correct in his analogy that a cybersecurity professional is a race car mechanic. For instance, when a car makes a funny sound, the car driver may have no clue what happened to the car. But the race car mechanic must be immediately about to think about the different possibilities that could have caused the issue, perform a root cause analysis, and drill down to the part of the car (could be a single part, could be structural) that caused the issue. Digging deep is a required skill.
2. Time
Keeping up with the latest in cybersecurity is difficult. Cybersecurity professionals complain of burnout rightfully because there is often too much to do. It is part of the job scope for cybersecurity professionals to be able to quickly internalise issues that happened, why they happened, and suggest solutions. All of these require time for self-study. I consider myself extremely lucky, especially with the COVID-19 pandemic, because I have a job, and the hours saved from commuting have translated into extra self-study hours.
3. To Get to the Door, You Need to Show Proof
Due to the COVID-19 situation, I have had my fair share of requests to look through résumés and suggest improvements to them. Two main issues seem to appear in those I have looked through:
a) The résumés do not indicate HR screening to advance to an interview due to the lack of certification OR
b) The résumés themselves do not allow interviewers to have meaningful discussions based on prior experience.
Juxtapose that with young people getting their first certification when they are still in school!
It simply makes it even more important to try harder.
Why Did I Write Such a Long Treatise?
Perhaps this is a function of Linkedin, where many seek to strut their credentials, or their opinions on the industry. In effect, I am doing the same.
But my intent here is not so much to make a direct reply to Naomi’s post on whether I agree or disagree with her. Instead, I thought it was a good opportunity to try to explain some of the basic areas in cybersecurity one might encounter. Because of the breadth of cybersecurity, it is in fact not possible to try to answer questions like, “Are IT fundamentals required for a cybersecurity job?” But all of us like short, summarised answers to these questions no matter how deeply flawed they may be. I dislike that approach thoroughly. Therefore, I decided to paint a basic picture of the cybersecurity landscape and attempt to look at it sector-wise.
I did not dwell into other roles such as incident responders and threat hunters. To be an excellent cybersecurity practitioner in one area is difficult. To attempt to do everything requires an institute. And stock answers simply do not cut it, just like how stock exploits do not work against the most modern of systems because the defence has already evolved. With an industry rapidly evolving like cybersecurity, cookie-cutter answers simply will not suffice.
In fact, to re-visit Naomi’s point:
You don’t NEED to know networking, computer hardware, operating systems, databases, or anything deeply technical to start in cybersecurity. All you need is a high level of comfort around technology. And you get this through constant exposure to IT.
Extracted directly from Linkedin post: https://www.linkedin.com/posts/naomi-buckwalter_cybersecurity-activity-6788161943971667968-1XuQ
I disagree here. I prefer to say that, you need to be uncomfortable with the technology that is around us today, think about what could go wrong, and how to make it right. As an entry-level cybersecurity practitioner, the word “technology” is likely to be broad, and that is good enough. But the mentality must be one of “trying harder” to make sense about the highly abstracted technological world around us.